network reconnaissance scripting
Python-nmap is a Python library that provides an interface to interact with the Nmap network scanning tool. Nmap is used for network discovery, service detection, and security auditing. By combining the power of Nmap with Python's flexibility, Python-nmap offers a convenient way to automate network scanning tasks and integrate them into your Python applications.
I have a post about using Nmap on your command line interface, why would we integrate Python and Nmap? Integration means tasks can be automated and we don't have to keep doing them over again. We can scan multiple hosts at the same time as well as filter the information and avoid common errors that may occur while running Nmap as itself.
Cybersecurity is full of repetitive tasks that take hours. We can use Python-Nmap scripts for both offensive and defensive security tasks that would normally take a while.
installing python-nmap
To begin set up your VM i’m using Kali Linux. I’m going to start by installing Python-Nmap with the command pip install python-nmap.
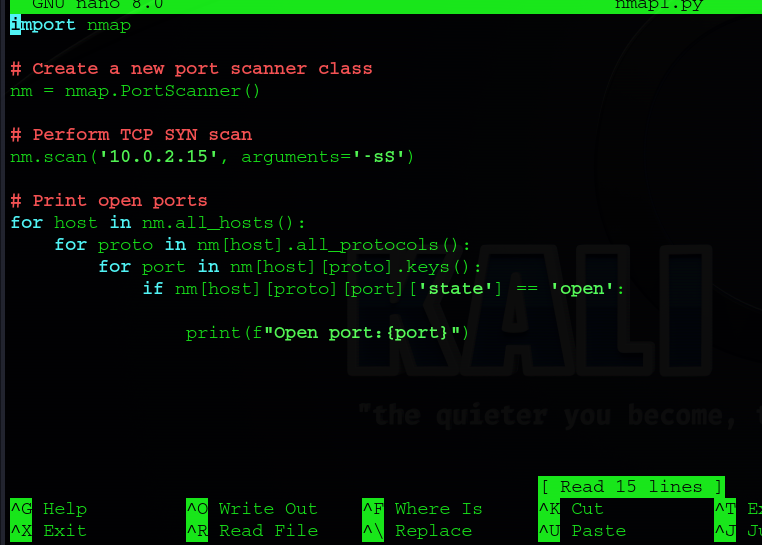
We can begin our code with the line import nmap to import python-nmap. As well, I am performing reconnaissance on a VM i have downloaded, take a note of the IP.
Our first script is a half-open TCP SYN scan. This works by sending a SYN packet our target and waiting for an SYN-ACK packet in return. however we don’t send a ACK back to complete the three-way handshake, hence the term ‘half-open scan’.
code explanation:
the import nmap imports the nmap library from the python index.
Create new port scanner class creates a simple interface for interacting with nmap.
We are using the -sS flag to perform a simple TCP SYN scan on our target. Telling nmap to scan the IP address of our victim and perform a half open scan. -sS scan are considered more stealthy as they don’t send an ACK packet back to complete the three way handshake and are less likely to trigger IDS systems.
The last section contains loops for what output the user recieves
for host in nm.all_hosts(): This loop iterates over all the hosts scanned.for proto in nm[host].all_protocols(): This loop iterates over all the protocols (e.g., TCP, UDP) for the current host.for port in nm[host][proto].keys(): This loop iterates over all the ports for the current host and protocol.if nm[host][proto][port]['state'] == 'open':: This condition checks if the state of the port is open.print(f"Open port: {port}"): If the port is open, this line prints the port number.
So our results will include the ports that are open on our victim machine.
I can perform another Nmap scan on my command line interface to double check my code.
service and version detection
So our TCP SYN scan gave us open ports but not much more information. To identify vulnerabilities we can perform a service and detection scan.
code explanation
Once the nmap module is imported, we can create a new port scanner class.
We can use the nmap -sV flag to perform a service and version detection scan.
The For loops iterate over all the hosts scanned as well as protocols in hosts, ports for the protocols.
For loops in ports iterates over the version and service running on the port and prints out each service and version associated with the port.
Our output gives us the versions and services that the open ports are running on. Why do we need to know this? because we can figure out was the versions of these services are vulnerable to.
creating more complex python-nmap scripts with scapy
Scapy is a Python module used for packet manipulation. We can use Scapy as its own tool or combine it with Nmap to perform more complex network attacks. I haven’t done any blog posts about Scapy before so we will go over the basics. So lets go over the main features of scapy:
Custom packet creation, scapy can modify all part of a packet. This is useful if we are trying to bypass security measures such as firewalls.
Ether() Creates an Ethernet header.
IP() Creates an IP header.
TCP() Creates a TCP header.
UDP() Creates a UDP header.
ICMP() Creates an ICMP header.
Raw() Creates a raw data layer.
show() Displays the contents of a packet in a human-readable format.
wrpcap() Writes packets to a PCAP file.
rdpcap() Reads packets from a PCAP file.
Creating and interpreting a variety of packet types.
Packet sending and receiving
send() Sends a packet to the network.
sr() Sends a packet and receives the response.
sr1() Sends a packet and receives the first response.
sniff() Sniffs packets from the network.
Packet dissection and analysis
layers() Returns a list of layers in a packet.
summary() Returns a summary of a packet.
show() Displays the contents of a packet in a human-readable format.
parse() Parses a raw packet string into a packet object.
to begin
To install Scapy, we are going to begin on our command line interface with pip install scapy. Next open up a file using nano text editor with the .py suffix.
The code above creates a simple TCP packet and sends it to our target machine.
Now we can try performing a TCP SYN can as we would with Nmap.
code explanation
First we import the Scapy module from the python library using from scapy.all import
Then define our target IP address Target_ip = “10.0.2.15”
List the ports that we want to scan (22,80,443)
The for loop iterates over each port that has been listed
packet = IP(dst=target_ip)/TCP(dport=port, flags="S") creates a TCP SYN packet for each port. The destination IP is our target IP.
sr1() sends a packet and waits for a response but doesn’t send an ACK packet back.
The Timeout argument sets wait time to one second and the verbose argument is set to 0 to suppress verbosity.
if response[TCP].flags == "SA": tells the command line to print open if the SYN ACK packet is received.
The elif loop prints on the condition that none of the ports are open.
Ok, now we know how to use Python-Scapy, how can we integrate it with Python-Nmap to create custom packets to perform network security scans? We can achieve a more comprehensive view of our target by utilising both Python Modules.
The purpose of this code to perform a scan that is more comprehensive and will bypass security solutions such as firewalls by sending fragmented packets that are harder to detect. Even though this is being performed in a home lab and staying stealthy isn’t a problem, we are imagining this is real life. What nmap doesn’t pick up on, scapy will and what scapy doesn’t pick up on, nmap will.
code explanation:
import Nmap and Scapy libraries for network scanning and packet manipulation.
Scan host function
takes target_ip and ports as arguments.
Performs a Nmap scan to get a baseline of open ports.
Iterates over specified ports, crafting fragmented packets using scapy.all.
Sends packets and checks for open ports based on TCP flags.
sends a half open TCP scan to the target machine with the -sS flag
Scapy uses the mf flag to fragment packets
The wait time is set to zero and there are no requirements regarding verbosity
The if loop iterates over the ports found open in the fragmented packet scan and prints the port if it is found open.
Compares the results found by printing all of the open ports in each python module.
if __name__ == “__main__” is used to control the execution of the code based on whether the script is run directly or executed as a module. When the script is run directly “name” is set to “main”. This means that the scan host function is only executed when the script is run directly.