burpe suite for sql injection attacks
what is an sql injection attack?
SQL (structured query language) Injection attacks occur when malicious code is inserted into an SQL query to manipulate the database. SQL attacks occur on web applications when the web application is vulnerable and hasn’t properly sanitized or validated user input before constructing SQL queries.
The server side handles client requests, if the code is vulnerable, an attacker can exploit it. Even if web traffic is running on port 443 and is encrypted. So it’s important to implement input validation, and parametize queries to protect against these attacks.
types of SQL injection attacks
Union Based SQL Injection- This uses the Union-based operator to perform an attack combining the results of multiple queries. When the application has a vulnerable SQL query that includes user supplied input. The attacker creates a malicious query using that contains the UNION operator, which is executed alongside the original query. Consider a vulnerable login page where the username and password are linked directly to the SQL query.
SELECT * FROM users WHERE username = ‘$username’ AND password = ‘$password’ ;
an attacker could inject the following input
‘ OR 1=1 UNION SELECT * FROM users; —
which would result in the modified query
SELECT * FROM users WHERE username = ‘ ‘ OR 1=1 UNION SELECT * FROM users; —
the 1=1 condition is always true to the UNION clause will be executed causing all the users data to be returned.
Error-based SQL injection- This is where the attacker exploits ERRORS returned by the application to extract information from the database. This attack can only be run from MS-SQL servers, the application returns an ERROR message showing the information the attack has asked for. Essentially, the syntax is being created that will intentionally return an error message containing information the attacker is after.
Blind SQL injection- In this attack, the attacker cannot observe the direct output of an SQL query and has to find out information based on the application’s response to different inputs. In this scenario the application will have a vulnerable SQL query that requires user-supplied input. The attacker’s query will modify the original query in a way that can be detected through the application’s response, and observe how the responses change based on the injection.
SQL injections based on method used to inject
SQL injection based on user input- Web applications process queries through forms which are input into the database for processing. If these arent sanitized before being accepted, it leaves room for attackers to inject malicious statements.
SQL injection based on cookies- Cookies are small text files stored on a users device to store session information and preferences. This is where the attacker exploits vulnerabilities int he applications cookie handling in order to inject malicious code.
SQL injection based on HTTP headers- HTTP headers are metadata sent between a web server and a client, containing information about request and response. In this casde the attacker modies the value of a vulnerable HTTP header to include malicious SQL code.
Second order SQL injection- A more complex SQL attack, in this case malicious code is injected into a web application indirectly and can lay dormant for a while. The data can be malicious in one context and normal in another context.
conducting an SQL injection attack
We are going to be using Burpe Suite to test out our own SQL injection attack. Burpe Suite is a platform used for penetration testing applications. It has tools for intercepting and scanning web traffic, it enables the scanning of traffic between a client and an HTTP/HTTPS web server.
In this example we will be using Burpe Suite community which has limited features compared to Burpe Suite professional but still has everything we need.
The key features are:
Repeater- The repeater allows us to manually modify and repeat HTTP requests. It works by capturing the request from the proxy tab or manually entering it in the repeater. Then you can modify the request by changing the URL, modifying the HTTP method (GET, POST, PUT, DELETE), adding or removing headers, and modifying the request body.
Proxy- The proxy is the man-in-the-middle intercepting web traffic and modifying requests. All traffic can be routed through Burpe Suite
Intruder- Allows for spraying endpoints with requests as well as custom payload injection, fuzzing. It works by specifying the target URL or parameters you want to attack, then you choose the attack type. Either Sniper, Battering ram, Pitchfork, or Clusterbomb, then you can create a list of payloads or payloads to send during the attack. Then launch the attack
Decoder- The decoder tool in Burpe Suite works to decode data that is not in a human readable format eg. base64, URL-encoded, HTML-encoded.
Sequencer- This is used to analyze the randomness of HTTP requests that have been captured using the Burpe Suite proxy. It determines entropy which is the measure of randomness.
To begin, we are going to download Burpe Suite, which is actually pre downloaded in Kali Linux. So we can just search for it.
We can then launch Burpe Suite Community Edition and accept the times and conditions before continuing.
We can click ‘next’ then ‘start’ to open burpe suite
configuring proxy
We are going to begin by configuring proxy settings in burpe suite so we can start intercepting traffic.
Under the proxy tab, click proxy settings. You should be able to see under interface what port its listening on. We can see interface 127.0.0.1:8080 we can modify the port the interface is listening on by pressing edit on the side columm
then we can go back and click on intercept is of to turn on intercept is on. This will allow us to intercept and modify requests.
Now we can open up firefox, then open up settings. We are going to search proxy settings
Once we open up our proxy settings, choose manual configuration and configure to the burpe IP
Now navigate to 127.0.0.1:8080 and download burpe certificate. The certificate needs to be installed as a trusted root so the browser can trust SSL connections made to burpe suite.
Ok, so now we go back to settings and search certificates.
Choose import, in certificate manager.
now if we go back to burpe suite with intercept turned on, we can see the browser requests.
penetration testing a web application
For this example we can use a deliberatley vulnerable web application ginandjuice.shop we are going to start.
network reconnaissance scripting
Python-nmap is a Python library that provides an interface to interact with the Nmap network scanning tool. Nmap is used for network discovery, service detection, and security auditing. By combining the power of Nmap with Python's flexibility, Python-nmap offers a convenient way to automate network scanning tasks and integrate them into your Python applications.
I have a post about using Nmap on your command line interface, why would we integrate Python and Nmap? Integration means tasks can be automated and we don't have to keep doing them over again. We can scan multiple hosts at the same time as well as filter the information and avoid common errors that may occur while running Nmap as itself.
Cybersecurity is full of repetitive tasks that take hours. We can use Python-Nmap scripts for both offensive and defensive security tasks that would normally take a while.
installing python-nmap
To begin set up your VM i’m using Kali Linux. I’m going to start by installing Python-Nmap with the command pip install python-nmap.
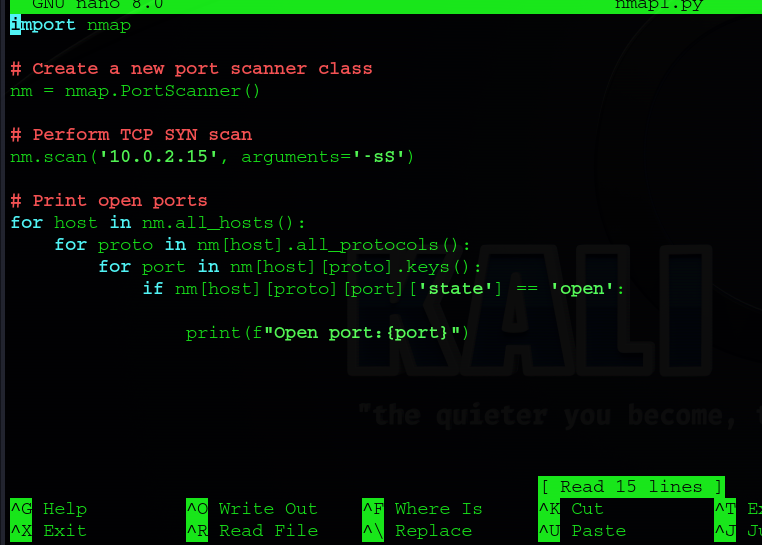
We can begin our code with the line import nmap to import python-nmap. As well, I am performing reconnaissance on a VM i have downloaded, take a note of the IP.
Our first script is a half-open TCP SYN scan. This works by sending a SYN packet our target and waiting for an SYN-ACK packet in return. however we don’t send a ACK back to complete the three-way handshake, hence the term ‘half-open scan’.
code explanation:
the import nmap imports the nmap library from the python index.
Create new port scanner class creates a simple interface for interacting with nmap.
We are using the -sS flag to perform a simple TCP SYN scan on our target. Telling nmap to scan the IP address of our victim and perform a half open scan. -sS scan are considered more stealthy as they don’t send an ACK packet back to complete the three way handshake and are less likely to trigger IDS systems.
The last section contains loops for what output the user recieves
for host in nm.all_hosts(): This loop iterates over all the hosts scanned.for proto in nm[host].all_protocols(): This loop iterates over all the protocols (e.g., TCP, UDP) for the current host.for port in nm[host][proto].keys(): This loop iterates over all the ports for the current host and protocol.if nm[host][proto][port]['state'] == 'open':: This condition checks if the state of the port is open.print(f"Open port: {port}"): If the port is open, this line prints the port number.
So our results will include the ports that are open on our victim machine.
I can perform another Nmap scan on my command line interface to double check my code.
service and version detection
So our TCP SYN scan gave us open ports but not much more information. To identify vulnerabilities we can perform a service and detection scan.
code explanation
Once the nmap module is imported, we can create a new port scanner class.
We can use the nmap -sV flag to perform a service and version detection scan.
The For loops iterate over all the hosts scanned as well as protocols in hosts, ports for the protocols.
For loops in ports iterates over the version and service running on the port and prints out each service and version associated with the port.
Our output gives us the versions and services that the open ports are running on. Why do we need to know this? because we can figure out was the versions of these services are vulnerable to.
creating more complex python-nmap scripts with scapy
Scapy is a Python module used for packet manipulation. We can use Scapy as its own tool or combine it with Nmap to perform more complex network attacks. I haven’t done any blog posts about Scapy before so we will go over the basics. So lets go over the main features of scapy:
Custom packet creation, scapy can modify all part of a packet. This is useful if we are trying to bypass security measures such as firewalls.
Ether() Creates an Ethernet header.
IP() Creates an IP header.
TCP() Creates a TCP header.
UDP() Creates a UDP header.
ICMP() Creates an ICMP header.
Raw() Creates a raw data layer.
show() Displays the contents of a packet in a human-readable format.
wrpcap() Writes packets to a PCAP file.
rdpcap() Reads packets from a PCAP file.
Creating and interpreting a variety of packet types.
Packet sending and receiving
send() Sends a packet to the network.
sr() Sends a packet and receives the response.
sr1() Sends a packet and receives the first response.
sniff() Sniffs packets from the network.
Packet dissection and analysis
layers() Returns a list of layers in a packet.
summary() Returns a summary of a packet.
show() Displays the contents of a packet in a human-readable format.
parse() Parses a raw packet string into a packet object.
to begin
To install Scapy, we are going to begin on our command line interface with pip install scapy. Next open up a file using nano text editor with the .py suffix.
The code above creates a simple TCP packet and sends it to our target machine.
Now we can try performing a TCP SYN can as we would with Nmap.
code explanation
First we import the Scapy module from the python library using from scapy.all import
Then define our target IP address Target_ip = “10.0.2.15”
List the ports that we want to scan (22,80,443)
The for loop iterates over each port that has been listed
packet = IP(dst=target_ip)/TCP(dport=port, flags="S") creates a TCP SYN packet for each port. The destination IP is our target IP.
sr1() sends a packet and waits for a response but doesn’t send an ACK packet back.
The Timeout argument sets wait time to one second and the verbose argument is set to 0 to suppress verbosity.
if response[TCP].flags == "SA": tells the command line to print open if the SYN ACK packet is received.
The elif loop prints on the condition that none of the ports are open.
Ok, now we know how to use Python-Scapy, how can we integrate it with Python-Nmap to create custom packets to perform network security scans? We can achieve a more comprehensive view of our target by utilising both Python Modules.
The purpose of this code to perform a scan that is more comprehensive and will bypass security solutions such as firewalls by sending fragmented packets that are harder to detect. Even though this is being performed in a home lab and staying stealthy isn’t a problem, we are imagining this is real life. What nmap doesn’t pick up on, scapy will and what scapy doesn’t pick up on, nmap will.
code explanation:
import Nmap and Scapy libraries for network scanning and packet manipulation.
Scan host function
takes target_ip and ports as arguments.
Performs a Nmap scan to get a baseline of open ports.
Iterates over specified ports, crafting fragmented packets using scapy.all.
Sends packets and checks for open ports based on TCP flags.
sends a half open TCP scan to the target machine with the -sS flag
Scapy uses the mf flag to fragment packets
The wait time is set to zero and there are no requirements regarding verbosity
The if loop iterates over the ports found open in the fragmented packet scan and prints the port if it is found open.
Compares the results found by printing all of the open ports in each python module.
if __name__ == “__main__” is used to control the execution of the code based on whether the script is run directly or executed as a module. When the script is run directly “name” is set to “main”. This means that the scan host function is only executed when the script is run directly.
What is kali linux?
and why do we use it for hacking?
And why do we use Kali for hacking?
Kali Linux is a distribution designed for ethical hacking, coming with around 600 hacking tools pre-installed, such as Nmap, Hydra, John the Ripper. It is very useful for penetration testing and malware analysis.
Kali Linux is built on a customised version of the Debian Operating Kernel. Which prioritizes the application of security patches very quickly to make sure the system is resiliant to threats. One of the reasons Kali has to be so secure is root access is automatically granted on Kali. So if an attacker gains access to your machine, there’s nothing stopping them. The kernel is also modified often to improve performance. To understand why this is important we need to understand the architecture of Linux.
linux architecture
-As we can see the arcitecture of Linux is divided into two spaces, the user space and the kernel space. The user space doesn’t interact with the hardware directly, the kernel space is the part that connects both.
-GNU C library allows it to switch mechanisms from the user space to the kernel space
-Kernel space/system space is simply for interacting with the hardware programs like RAM and hard disks. The system call interface will make requests to the
kernel such as allocate or dellocate memory.
-the architecture dependant kernel code is what bridges the gap between the kernel and hardware and handles the boot sequence and initial loading of the kernel.
-user applications refers to the interface
legal use and ethical hacking
Kali is designed to be used for ethical hacking. What makes hacking ethical?
Ethical hacking is when we identify vulnerabilities on a system before adversaries do. We use kali to attack a system while authorised and see if we can gain access, if we can gain access the developers or owners know what they can do to patch those vulnerabilities so they arent exploited at any point.
Cyber threats are constantly evolving, hackers only have to be right once, cybersecurity teams have to be right everytime. Constantly running penetration tests against a system will result in better security and a robust system.
Essentially, malicious hackers exploit a system to cause harm and ethical hackers exploit a system to create better defenses.
how to install kali linux
First we need a VirtualBox manager for our machine. Downloads – Oracle VM VirtualBox download via the link.
and then we need to download our iso image for Kali Linux Get Kali | Kali Linux
Ok so once we have these, we are going to open up oracle VirtualBox. We are going to press the ‘new’ button. Where it says iso image we are going to select our kali linux iso image.
How many cores and how many mb you want to allocate depends on the tasks you are using your machine for.
then follow through with the prompts provided until the finish button comes up
We can press start to launch our machine
website downloading & mirroring
how to mirror websites and bypass copyright and crawler prevention
How to mirror a website
Some people are into data hoarding, some people are also into phishing, and some people just think a website is useful and should be kept for further use. Website mirroring, the process of creating an exact replica of a website on a different server, can be a powerful tool when used ethically and responsibly. However, it’s essential to understand both the benefits and potential drawbacks.
httrack- command line tool
Httracker is a powerful tool we can use to save and mirror websites. There are several examples where this is tool is crucial. Say you need to mirror a website for phishing, or theres useful resources on this website that others should be able to access. Either way this is how we can use Httrack.
to install in kali linux we are going to use the command ‘sudo apt install httrack’
Then we need to create a directory to store our website using the command ‘mkdir website’ or name the directory whatever you like.
We are going to use the ‘cd’ command to open the website directory. Then ‘httrack’ to run the httack application
Httrack will give us several options below. I am entering the project name as ‘httrack’ . we need to define the base path ‘/root/website’ . I am using the Vulnweb pentest page for this blog because I feel like they probably won’t mind me mirroring their website, so I am going to copy and paste their URL under ‘enter URLs’ ‘login page (vulnweb.com)’ . I would also recomend practicing on pages like this before you start mirroring other websites.
Httrack provides us with option for switches below. Under actions we can choose mirror all of the URLs or mirror just the website. The different wildcards are for defining filters
+*.gif accept all gif images
-*.js exclude all files with the extension js
+/images /.jpg include all files in that directory
We can define recurse level with the ‘-’ flag followed by the recurse level we want
-0 only downloads the start page
-1 downloads the start page and all links directly from it
-2 downloads as many pages as possible including links and links from those
Then we choose ‘Y’
Then use the ‘ls’ command to list your files under the website directory
Then ‘cd vulnweb’ because that is what my file is called
‘ls’ will list the files I have in Httrack. I’m going to use the command ‘python -m http.server’ . The ‘python’ command will use pthon’s subprocess module to execute httrack commands. The ‘-m’ command will tell python to run the module as a script. ‘http.server’ will run the HTTP server module.
Now that we have been given our http server we can navigate to ‘http://localhost:8000’ to run our mirrored website
winttrack- gui
Wintrack is the GUI equivilent to httrack which can be downloaded at HTTrack Website Copier - Free Software Offline Browser (GNU GPL)
Here we will be interacting with a graphical interface to copy our website of choice
Once downloaded, we will launch the Httrack application and press ‘next’
I’m going to name my project ‘test website’ and save it to the website directory
Here we are given the option to choose an action where we can test links, download all links to fullly mirror the site. In this case I am just mirroring the front page.
Once we click ‘next’ we are taken to the page where our website mirror is downloaded
Then we can click ‘browse mirrored website’
And we have our mirrored website saved on Wintrack
Mirror prevention measures- how can we bypass them?
Httrack can be a hit or miss, its easy to mirror a website front page like we have above. What if we are trying to mirror a website and the website has measures to prevent it.
One technique some websites use is robots.txt, which prevents the website from being indexed if some derivatives are applied.
IP Blocking is another technique where websites will recognise the IP of certain crawlers trying to access and they will block them. This method can potentially be bypassed using a proxy server or VPN.
User Agent Detection works by analysing the string request sent by an application, if the user agent seems like a mirroring tool, the website may block it. Bypassing user agent detection is difficult but can be achieved through using proxy servers, rotating IPs to avoid being flagged as a bot. We may be able to avoid user agent detction by mimicking a real users browser.
Rate limiting to limit the amount of requests one IP address can send, this can be bypassed with a proxy server too.
Legal Action, some websites a copywrited and it is very illegal to copy them. Owners of the website will not be happy with your actions so do not do illegal stuff for malicious purposes.
-wget
Wget has switches that we can use to bypass mirror prevention measures from secure websites. There are several tools I am going to use to attempt to find vulnrabilities in my test website (I am not actually doing anything illegal). However wget is more difficult to use then httrack.
The basic syntax for wget is ‘wget {website URL}’ . before using wget navigate to a directory where you want to store your website
If we want to download the whole website including links, we are going to use several switches.
-r which will enable recoursive downloading
-p downloads necessary files including such as images and CSS to display html pages correctly
-E converts html files to .html
-K converts the links in downloaded HTML files to point to local files
-np Prevents wget from going up parent directories, ensuring you only download files within the specified domain.
Here in this attempt, the website i tried to copy has website prevention measures
I’m going to try bypass these measures using the user agent string script so it looks like I am coming from a legit website as many websites block crawlers and I dont want to be blocked, the syntax and script I am using is:
wget --user-agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36" -r -p -E -k -np (domain url)
Success! but I want the whole website
So we are going to need to utilise some more scripts to achive the results we want. I want to fully mirror the website so I am going to also utilise these scripts ‘--mirror --convert-links --adjust-extension --page-requisites --no-parent’
— mirror will enable recursive downloading, treating the server as a mirror.
— convert-links converts links in HTML files to relative paths for offline viewing.
—adjust-extension Adds appropriate extensions to downloaded files (like .html, .css).
—page-requisites Downloads all necessary files for page rendering (images, CSS, etc.).
—no-parent Prevents going up directory levels.
we can also use the ‘—wait’ and ‘—random-wait’ command to avoid overloading the server
I’ve written a simple bash script to mirror websites with wget because I am lazy and don’t want to write commands over and again. I’ve used to scripts as well as the switches and agent string mentioned above, you can use the same script just swap out the website URL for the one you want. Warning, this script may take a while to run because it utilizes many commands and switches.
I’m copying and pasting my script below in case someone finds it useful
#!/bin/bash
website=http://testphp.vulnweb.com/login.php
mirror_dir="website_mirror"
user_agent="Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36"
mkdir -p "$mirror_dir"
cd "$mirror_dir"
wget --mirror --convert-links --adjust-extension --page-requisites --no-parent --user-agent "$user_agent" -p -r -E -K -np "$website"
once I run my script im going to navigate to where it is stored
I’m then going to navigate to my file manager and locate the files under my Kali Linux folder
Here I am given every file from my mirrored website
And here we go, our mirrored website.
If you are mirroring websites, please respect copyright laws and do not use this for unethical purposes.
NMAP- NETWORK MAPPER
how to use a powerful reconnaissance tool
Installation:
Pre-installed on Linux
Windows: https://nmap.org/download
To verify is nmap is isntalled nmap —version
NMAP, short for network mapper is an open source, Linux command line, tool used for port scanning and discovering hosts on a network. a useful reconnaissance tool for penetration testers. Some of NMAPs features include ping sweeps, port scanning, OS detection, version detection.
NMAP can allow you to find devices running on your network and unused applications.
In one scene in the matrix, Trinity uses NMAP. She uses NMAP to find a vulnerable SSH server and exploits it using SSH1 CRC32 exploit, to hack the city power grid.
how does nmap actually work?
Nmap uses raw socket scans to send raw packets to the ethernet layer of your network which bypasses the TCP/IP processing. Essentially communicating with an IP address directly,. Other sockets such as datagram sockets or stream sockets revive transport data that is from the transport layer and only contains the payload, this means there is no information about the source of the data. One of the downsides of this is UNIX systems will restrict raw packet communication to root users and admins to prevent users abusing priveledges.
The reason NMAP is structured like this is because, most operating systems will have a raw socket API that allows programs to access the network interface card (NIC)/ethernet card/network adapter directly. By bypassing other communication protocols, it gives Nmap more control over packet creation and transmission.
port states
During a port scan nmap will show you the different states ports can be in. This tells us if the target is vulnerable or not.
open- application is open and listening for connections on the port
closed- cannot make connections as ports are closed
filtered- port is protected by a firewall, unable to tell if port is open or closed
unfiltered- responsive to probes, but nmap is unable to tell if it is open or closed
open/filtered- appears when port gives no response
firewalls and bypassing them
Secure home networks will have firewalls configured. Firewalls definitely make network scanning more difficult as they will block packets. Firewalls can be configured to block packets on ports commonly used by nmap such as TCP ports like 21,22,23,80,443. It can also filter traffic basic on certain protocols like IMCP, TCP, UDP to stop different scanning techniques.
To bypass a firewall, it is useful to know the rules that the firewall has in place. Knowing whether or not the network you are scanning has IDS/IPS in place. A decent Firewall should be updated regularly and should be able to detect signatures as well as behavioural anomalies.
It’s important to understand the types of firewalls we are dealing with.
packet filtering firewall- examines each packet based on the source IP, destination IP, ports, and protocols. This is a basic firewall.
stateful inspection firewall- keeps track of session state, Blocks or allows connections based on context.
Proxy firewall- examines traffic at the application layer of the network and allows more granular control over data and applications.
next generation firewall- Almost a security solution on its own, this is an advanced firewall that combines multiple security solutions and techniques like IDS/IPS, Malware detection.
ACK scans are one of the first techniques we can use to try bypassing a firewall. An ACK scan send TCP packets with only the ACK bit set. A normal TCP connection works as a three-way-hanshake where a SYN a SYN-ACK and an ACK packet are sent back and fourth. The basic syntax for an ACK scan is ‘nmap -sA {target IP address}’ . The output of an ACK scan will show ports as either filtered or unfiltered, unfiltered can still mean that a port is closed.
We can also use the -f scan to fragment packets. Modern firewalls are becoming more efficient at detecting fragmented nmap packets so this isn’t a guaranteed win. Normal packets sent to a destination a transmitted as a complete unit with all the information data and header within a packet. Fragmented packets are broken down into smaller pieces called fragments. This normally occurs when a packet exceeds the MTU of a network link and the packet is reassembled at the destination. This can bypass firewalls by either overloading the firewall, similar to a DDoS attack where all of its resources are being used to inspect the packets. Some firewalls may not ressamble the fragmented packets correctly which allows our packets to slip through, undetected. Other firewalls may not be capable of handling fragmented packets or it may be a vulnerability.
The basic syntax for a fragmented packet scan is {nmap -f (target IP address) we can also choose how many fragments we would like our packets broken into by offsetting the maximum transmission unit if we use the flag {-- mtu} we could add a value like 16. The MTU value has to be a multiple of 8 bytes and smaller values will make the scan longer.
TCP Null scan can be used as well, we use the TCP scan if we do not have raw socket rpiviledges. the (-sN) flag sends a packet with no flags set which can sometimes bypass firewalls.
basic scans:
a basic scan: {target host} is replaced with the IP address of the host
this will provide a basic scan
the host may respond to pings
open ports or services running
TCP scan- focuses on TCP ports, common communication protocol. This works by nmap sending a SYN to the target port but completes the three-way-handshake by sending an ACK back. If the target send a SYN-ACK back the port is considered open. This scan is useful when raw socket privileges are not available or we are scanning ipv6 networks. remember that nmap has less control over the connect call with a TCP scan then when using raw packets to connect, and has to complete full connects rather then a half open SYN scan.
Diagram from nmap.org showing TCP Nmap connection
basic syntax for a TCP scan
UDP scan- for DNS and gaming servers. UDP scans are generally slower and run on ports 53, 161/162, and 67/68. UDP scans work by sending empty packets with no payload (no data present). So the output of UDP scans will be different. If there is any response from the port it will be marked open.
SYN scans- faster than TCP scans but can trigger firewalls, note these will only be able to gather information if their is no firewall present.
OS detection- find out the operating system of your target host
Port scanning
to scan a specific port on a target, for example 80 we would use the -p80 flag
we can specify the range of ports we want to scan with a dash between the first and last port. for example -p 1-80
we can also use stealth scans to avoid firewalls or intrusion detection systems (IDS)
the flag -sS sends half open connections
the flag -MA uses fragmented packets to bypass packet filtering
we can also customise the output of our scans
-oA {filename} can save the scan in outputs such as grepable or XML
-oG {filename} can save the output in graphical format
verbosity
The -v flag (verbose) can provide additional details from your scan.
There are nine levels of verbosity available.
-4 provides no output
-3 no output but provides you with error messages to see if scan has failed
-2 no output but with warnings and error messages
-1 shows run time and statistics
0 default level, shows packets received as well as other information
1 same as 0 but provides protocol details, flags, and timing.
2 provides more information on sent and received packets
3 shows the complete transfer of sent and received packets
4 like 3 but with more information
nmap scripting engine
NSE allows users to write and share simple scripts using LUA programming language, which can automate different networking tasks.
the basic syntax for using scripts is either the -sC flag to enable the most common scripts or —scripts to specify which script
NSE scripts are broken down into categories
{auth} provides scripts to deal with authentication mechanisms on target systems
SSH-login attempts various logins and usernames to access an SSH server
similar to ssh-login but works with FTP server
{broadcast} gathers information about devices on a network using broadcast techniques. it doesn’t target hosts directly, instead sends packets to a network to find targets that respond.
sends ping requests to a network address
used for service discovery in local networks (multi-cast domain name system). useful for identifying devices such as printer and smart tvs.
{brute} for brute force password cracking and authentication (there is an overlap between auth category and brute category)
guesses usernames and passwords for my-sql databases
{discovery} to find out more about services and networks
checks if anonymous login is allowed on an ftp server
NMAP’s basic scans already provide good coverage when trying to gather information. trying to gather more detailed knowledge is where we start needing to use scripts.
They can be a valuable tool for vulnerability assessment, automation, and penetration testing. remember never use NMAP for unethical purposes.
what are zero-days
And how do we exploit them?
And how do we exploit them?
Zero-days refers to a vulnerability found in a system before the before the developers find the vulnerability. Zero-days are pretty dangerous as the developer has not had a chance to fix the exploit first.
A Zero-day attack occurs when an attacker exploits a vulnerability before a patch or fix has been released for this vulnerability. As soon as a zero-day is discovered by the manufacturer it stops being a zero-day.
we can liken the usage of zero-days to the CyberKill Chain (which I also have a blog post about). The process of exploiting these vulnerabilities is the same where the vulnerability is discovered, an exploit is created, an attack is carried out etc.
how do attackers find zero-day vulnerabilities?
There are many different ways to find zero-days as most software has some vulnerability even if it isn’t huge. I have used the house or castle analogy often in my blog, let’s go back to it. Imagine a software system as a castle, it’s big and has plenty of defenses, however, there’s probably some part of the castle where maybe a brick is missing, or there are vines growing up the side that could be climbed by someone small. discovering these vulnerabilities isn’t easy but it can be done if you understand the castle architecture, maybe what types of materials were used and maybe you understand about common vulnerabilities within this type of material. It’s similar to software systems, it’s difficult to make a perfect software system.
Some common techniques used are:
fuzzing- This is when attackers send abnormal data to an application to see how it reacts. essentially throwing random data at software to see if it breaks or if there are vulnerabilities present.
reverse engineering- essentially analyzing components of the code and how it interacts with each other. It allows attackers to find weak points that potentially can be exploited. It starts with the machine code being disassembled into code more readable by humans normally achieved using tools such as IDA Pro, Ghidra, and Hopper. Then there is a decompilation stage where the attackers will attempt to convert the assembly code into a programming language such as C or Java, which can be difficult as information is lost during compilation. Then dynamic analysis where the code is run in a controlled environment, to observe behavior and identify any vulnerabilities.
Automated scanning tools- SAST (static application security testing) which examines source code without executing it for vulnerabilities such as buffer overflows, SQL injection, and cross-site scripting. Or DAST (dynamic application security testing) which simulates real-world attacks to discover web application flaws.
social engineering- attackers can use social engineering techniques to convince employees to give up information.
well-known zero-day attacks
Stuxnet computer worm
2022 chrome attacks
wannacry, eternalblue exploit
log4shell
how can we protect against zero day attacks?
patch management / updating software and applying patches regularly
threat intelligence feeds, stay updated on external threat intelligence.
zero trust architecture, use constant authentication and least privilege access to prevent lateral movement across a network.
penetration testing, deploy ASM tools as well as hire penetration testers to hunt for vulnerabilities.
network vulnerability testing
how to pentest your home network
Your network may be hackable. There is probably some vulnerability present that if a hacker scanned your wifi IP, they would find a backdoor into your network.
This is going to include a few ways to scan your network in depth for open ports, how to hide your IP, and how to harden your network to prevent access from people with malicious intentions.
First of all. What is a network? A network is a series of devices connected together through wireless or ethernet connections. Your router acts as a server, and contains the data that is shared. Each server has a public IP address that can be shared, this is why we use VPN’s when visiting some websites, a VPN shows a different IP to our actual one, so people can’t access our physical location by searching with our IP.
Basic diagram of how a home network is structured.
endpoints send data packets to routers with an IP address attached kind of like how you would send a parcel with an address on it.
router/switch reciveves data packets from endpoints and chooses the best path for them to take across a network. This is reliant on knowing the IP address or destination of the data packet.
Finding your IP address is pretty easy try googling it and it will appear. Your external IP address is shown to websites when you visit, note that it isn’t your devices IP (internal) but your external network IP. So nobody can find your exact device on the network but they can see your location approximately.
If an adversary gains access to your public IP address they can do several things with it. They can scan for vulnerabilities and find open ports to gain access to your network.
pentesting to find vulnerabilities in your network
To scan for vulnerabilities in our network, we need to scan from outside our own network. To achieve that, we are going to set up our own Linux server outside our network. Its best to use a cloud computing platform. I’m going to be using Linode.
Once i’m in my Linode account i’m going to click ‘create’ and ‘Linode’
follow the prompts, and choose an area relatively close to where you live.
once our server is created click ‘Launch LISH Console’ to launch your server
the username to login will be ‘root’ and the password is the one you created while setting up
I would reccomend using the command ‘apt-get update’ to make sure your server is able to packages
as well as ‘apt-get upgrade’
then use the command ‘apt install nmap’ to install nmap on your Linux server
we’ll start of with a ping scan to see if host is running (I’m not including my actual ip address)
the -sT flag is to perform a TCP scan
My nmap is saying host is down when it is not down, meaning my network has a firewall in place. I do have an Nmap tutorial on my blog which has information and tips for bypassing firewalls however some are diffcult to bypass with my current skills. so what I have going to do is run another scan and fragment the packets I send to hopefully allow them to pass through without being recognised by my firewall.
I’m using the - -mtu flag to fragment my packets by 16, you can also use the -f flag. apparently my firewall is configured to handle fragmented packets so we are going to try another way.
I’m going use a pretty easy website pentestools.com to see if its my configuration or the host I am trying to scan
as we can see here, my home network has zero open ports.
Discovering hosts on a network
Maybe we want to see if someone is already inside our home. ARP (address resolution protocol) works by sending requests to all possible host IP addresses within a network range that has been specified.
First, we can learn about the subnet mask within our home network. If I use the command ‘IP add’ in kali linux it will tell me the host IP under inet. An IP address is split into four octets, the first three represent the network portion of the IP address and the last represents the Host portion.
When we scan with Arp-scan we neet to specify the interface. I’m also using sudo -i to give me root privileges without having to use sudo command everytime.
when I scan from my Kali Machine within from my eth0 interface I am given three hosts above and the blank is the other IP addresses in my network.